API Security Testing Basics!
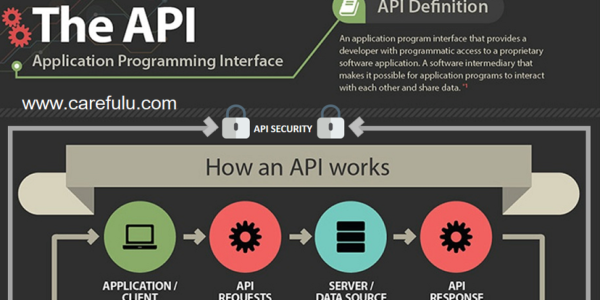
The API is a crucial component of contemporary net and cell applications, and SaaS. APIs, by definition, reveal business good judgment and personal data consisting of Personally Identifiable Information ‘PII’, and as a end result, they have grow to be a famous goal for hackers.
Rapid advancement could be tough with out comfy and secure APIs. Therefore, it becomes essential to carry out API security trying out earlier than a horrific actor receives keep of it for you.
RESTful API Security Testing Fundamentals
There are simply four fundamental suggestions to obey in relation to appearing protection assessments on RESTful APIs. However, as is the case for all exact ideas, bringing them into reality can be tough.
The beneath are the simple policies, which may be without problems incorporated into a web server:
- Discard Incorrectly Typed Inputs
Where a null is undesirable, inputs which are null ’empty’ need to be refused. - Refuse Incorrectly Sized Inputs
The more tough ideas necessitate a thorough interpretation of the ideal set of values and users, which can be hard to deduce without first information how a REST API might be used.
Three. For a Provided Input Value, the API have to Deliver the Anticipated Output.
If the enter realm and output variety are minimal e.G., Phone numbers, age, this will be without difficulty examined. It turns out to be very tricky while growing permissive RESTful APIs that permit users to send their very own content material e.G., in electronic mail and social networking sites.
Four. Refuse Input values Beyond the Needed Domain
This is easy when the domain is straightforward as an instance, date of delivery should be greater than zero. However, users furnishing the statistics complicates the procedure e.G., imparting a consumer to record add endpoint can be a volatile and an large venture to at ease.
Five. API Must Provide Data to Authorized Users Only
This can be simple to put in force if permissions are already specific and assets are prepared according to their permission level. However, authorization remains a difficult challenge to conquer, with the presence of many multibillion-dollar companies consisting of Okta to help.
The majority of APIs aren’t very well checked which guarantees that they fulfill these necessities. Due to this, APIs breaches are not unusual and there are businesses like OKTA that offer a shield on top of APIs.
Therefore, it’s miles always first-class to perform powerful security trying out on APIs to defend them towards attacks.
Elements of an API Security Testing
Security Testing
Security Testing facilitates in validating fundamental safety necessities. You want to answer the subsequent questions earlier than appearing the testing:
Exactly what type of authentication is needed to apply the API, i.E. How do you decide an cease person’s identification?
Identifying the form of encryption getting used on the facts that is saved, and whilst is the facts decrypted for transmission?
What are the situations that allow users to gain access to assets?
This is the first step in securing APIs, and it’s going to help avoid main security problems.
Penetration Testing
Penetration testing lets in you to bolster the outdoors floor of your software from security weaknesses which could have crawled in all through the improvement method. In this step, external aspects of the API are attacked in a premeditated fashion in a managed surroundings net app pen testing. This can be finished by the use of computerized equipment which includes Netspark or Acunetix.
While performing API Penetration Testing, observe the steps below:
Make a listing of capability security troubles applicable to the software.
Arrange the gadgets found in the above steps in keeping with their threat. You can talk to the OWASP Top 10 listing if you have any doubts approximately the danger a selected sort of difficulty poses.
Create requests and periods that encompass the test instances and deliver them to the server preferably from each the internal and external to the community.
If an unauthorized person can advantage access to the tool, log and patch the problem.
Fuzz Testing
The final step in a security auditing section is fuzz testing, which involves pushing an API to its limits. This may be accomplished by sending a massive quantity of requests to it. Each request must have varying data in as many resourceful ways as feasible to cowl the risks arising due to sending an extensive number of requests. These flaws may additionally result in Denial of Service or Overflow assaults.
Performing Security Test on an API
Testing an API involves sending requests to an endpoint of the application being examined by the use of an HTTP client. There are lots of unfastened HTTP customers available, however the most well-known ones are Postman or Insomnia amongst these options.
The DevOps lifecycle may be improved by way of automating components of the Security Audit method. The Fuzz Test and the Security Test, covered within the previous phase, are the best to automate.
Step 1: Determine Security Requirements
You ought to first don’t forget the overall specifications earlier than making plans a safety check on an API. This includes answering questions along with:
Is API on hand thru HTTPS and does the API require a TLS/SSL certificates?
What authorization instructions exist for the utility’s diverse resources?
How does the authentication system paintings? Is it using a 3rd-party OAuth carrier?
What is the API’s attack floor?
It’s critical to have a clean idea of what constitutes a skip or fail to your assessment even as you’re answering the above questions.
Step 2: Setting Up a Testing Environment
It’s time to installation an software surroundings for trying out as soon as the scope of the check has been installed. It’s fair to apply the conventional staging environment for smaller applications. For bigger applications, it’s first-rate to set up a different environment for trying out larger programs. It can be completed via replicating the sources inside the staging environment or by the use of a device like WireMock for simulating.
Step 3: Performing a Sanity Check on Your API
Send off a couple of requests to the API to verify that everything has been well installation.
Step 4: Assessing the Input Fields
It’s important to remember what each parameter does and the diverse combinations that each parameter will take, before creating individual check cases. This lets in you to describe rare instances (values which might be only slightly legitimate). Also, it helps to identify the parameters that are quite at risk of injection assaults together with SQL injections.
Step five: Creating and Running the Test Cases
After you’ve installation the take a look at surroundings and recognized some capability edge instances, you can formulate and run checks, comparing the real output to the anticipated output. You need to organization those in keeping with the type of check being executed as part of exceptional practice.
Wrapping Up
Now, you will have a clear know-how of your software’s protection reputation. It will even act as a toolkit for ensuring that no primary security problems make it to manufacturing deployment. If this sounds too daunting, you can usually take the help of safety experts at Astra Security.

 For all latest news, follow The carefulu Google News channel.
For all latest news, follow The carefulu Google News channel.




